Multi-Factor Authentication (MFA)
What is Multi-Factor Authentication?
Multi-factor authentication (or multiple factor authentication) is a characteristic requirement of an authentication service that requires more than one authentication factor for successful authentication. It requires at least but not limited to two factors of:
- Something you know (like a password)
- Something you have (like a token, YubiKey, or mobile phone)
- Something you are (like your fingerprint)
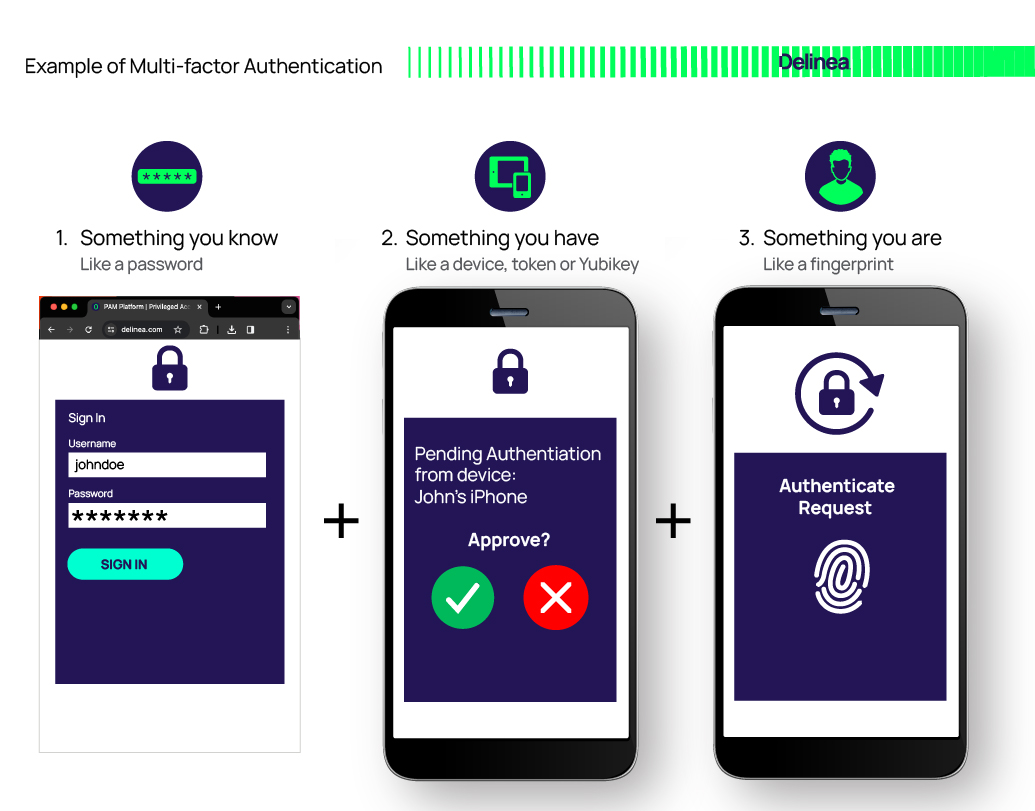
Within the context of IT, human user authentication is synonymous with login. However, two-factor authentication (2FA), multi-factor authentication (MFA), and adaptive multi-factor authentication (AMFA) can be applied to both login as well as step-up authentication which occurs after login; for example, during privilege elevation or checking out a vaulted credential.
2FA requires two of these factors for the user to prove who they are. MFA requires any number of factors greater than one. For example, two factors, or all three.
AMFA extends MFA by taking user and behavioral context into account, leveraging machine learning and a behavioral analytics engine. Over time, the AI and analytics engine learns a user’s typical behavior and uses this as a baseline to compare current activities. This results in a risk score that can be used in an access control policy to grant or deny access. One example might be a policy that simply allows access if the risk score is low, prompts for MFA if it’s medium, and rejects access and notifies IT security if high.
Why should your organization use MFA everywhere?
Why MFA is essential
Multi-factor authentication (MFA) has become essential for organizations to strengthen security beyond just passwords, which can be vulnerable to attacks. Adding a second factor enhances protection and reduces the risk of unauthorized access.
- Strengthens organizational security: MFA improves security by requiring not just a password but an additional identity verification factor to gain entry. This safeguards against brute force attacks, phishing, and stolen credentials.
- Passwords alone are vulnerable: Usernames and passwords can be compromised through phishing, sharing, or credential stuffing. MFA adds another barrier that makes breach exponentially harder if one factor is stolen.
- Necessary for digital transformation: As business shifts online, MFA provides enhanced security for remote workers, cloud apps, online transactions and more.
- Defends against cyber threats: By requiring extra identity confirmation, MFA helps thwart account takeovers, data breaches, and fraud from stolen credentials.
With mounting threats, MFA has become essential for access management and authentication. Adding a second factor makes infiltration of systems protected by MFA extremely difficult.
How MFA works
MFA enhances security by requiring users to provide additional verification factors beyond just a password when logging in. This added layer of identity confirmation makes unauthorized access much more difficult.
- Requirement of extra verification: MFA necessitates extra forms of verification such as one-time passcodes, biometrics, security keys, or authenticator apps in addition to a password.
- Common MFA factors and methods: Some frequently used MFA factors include one-time passcodes via SMS, email, or apps, physical hardware tokens, biometrics like fingerprints or facial recognition, and security keys. These can be used individually or in combination.
- Adaptive MFA and risk-based authentication: Advanced MFA solutions analyze context like user behavior, location, network etc., to adapt authentication demands based on risk levels detected.
- Role of AI in MFA: AI and machine learning aid MFA by recognizing trusted devices, building access profiles, and identifying suspicious logins to step up security as needed.
By necessitating an additional factor beyond a password, MFA significantly reduces the chances of infiltration by cyber criminals even if credentials are compromised.
Types of MFA authentication methods
MFA leverages multiple authentication factors across different categories for enhanced security:
- Knowledge-based factors: These verify identity using something the user knows, like a password, PIN code, or answers to secret questions. Though susceptible to guessing, knowledge factors provide customizable options.
- Possession-based factors: These authenticate via something the user has physically, like security tokens, mobile apps, certificates, or security keys. Possession factors safeguard access with unique codes sent to user devices.
- Inherence-based factors: Inherence factors employ biometric verification through fingerprints, facial recognition, retina scans, and other unique user attributes.
- Location and time-based authentication: By evaluating user location, IP address, or access patterns over time, adaptive MFA solutions can apply additional controls based on detected risk levels.
- Adaptive and risk-based authentication: Context-aware MFA dynamically analyzes data like user behavior to step up authentication requirements in response to suspicious activity.
Advantages of MFA
Implementing MFA offers significant security advantages:
- Enhances protection beyond vulnerable passwords that are prone to attacks like phishing and brute force. Adding a second factor makes unauthorized access much harder, even if credentials are compromised.
- Controls access to sensitive systems and data by requiring additional authentication, preventing account or network infiltration.
- Provides flexible options like one-time codes, biometrics, and security keys to meet an organization's specific security needs.
- Helps meet compliance requirements that mandate strong access controls and audit trails.
- Defends against threats like phishing that can lead to major data breaches by creating an extra barrier beyond stolen credentials to prevent account takeovers.
Disadvantages of MFA
Implementing MFA also poses some challenges:
- Adds complexity for both end users and IT administrators. There is a burden of managing tokens, biometrics, mobile apps, and advanced systems. Adequate training is essential.
- Occasional technology issues could temporarily prevent access if secondary authentication factors become unavailable. Backup options should be in place to prevent disruption.
- Additional dependencies on separate authentication systems create more potential failure points. MFA systems need to be highly reliable and have redundancy.
- The password reset process with MFA introduces a brief period of lowered security that attackers could attempt to exploit. Safeguards need to mitigate this risk.
- In some cases, the extra authentication steps may inadvertently block access for legitimate users who have lost or damaged their devices. Backup options help prevent an accidental lockout.
So while not perfect, MFA's security benefits dramatically outweigh potential drawbacks for most organizations.
As digital transformation accelerates, Multi-Factor Authentication has become essential for robust identity and access management. By requiring an additional factor beyond just a password, MFA dramatically reduces the risks from compromised credentials and account takeovers.
While setting up MFA introduces some complexity, the security benefits far outweigh the drawbacks for most organizations. Following best practices around flexible options, user education, and context-aware controls ensures smooth adoption. MFA is a powerful tool to counter emerging threats in an increasingly online world.
For more on implementing secure and usable MFA, see the following resources:
Blog Posts
Best Practices for Multi-factor Authentication
What is Adaptive Multi-factor Authentication?
Why Organizations need Adaptive Multi-factor Authentication
Single-factor Authentication (SFA) vs. Multi-factor Authentication (MFA)
Two-Factor vs. Multi-Factor Authentication
Whitepapers
Best Practices for Verifying Privileged Users with MFA Everywhere
Video Demos
MFA at Server Login on a Linux Machine
MFA Everywhere: Vault login to Server Login

