Top takeaways from the 2021 Verizon Data Breach Investigations Report

Joseph Carson
The 2021 Verizon Data Breach Investigations Report (DBIR) is here with the latest news and trends on the past year’s data breaches and security incidents. The Verizon DBIR is one of the industry’s top reports providing us with an indication of how well, or how poorly, our security efforts are performing, as well as giving detailed insights into what techniques cybercriminals prefer to use in exploiting our vulnerabilities.
Understanding the latest cyber criminal techniques and processes is invaluable in planning and implementing our best defenses, ensuring we make it more difficult than ever for cybercriminals to be successful.
One of our main jobs in cybersecurity is to force cyber criminals into taking more risks, as the more risks they take the more noise they will make
This 14th edition of the DBIR report includes 88 countries, 83 contributors, 79,635 incidents, and 5,258 data breaches, making it a truly global report with valuable insights everyone can learn from.
This year’s report showed another decline in the number of incidents analyzed. However, the number of data breaches showed a significant jump up from 3,950 confirmed data breaches in the 2020 report to 5,258 in 2021.
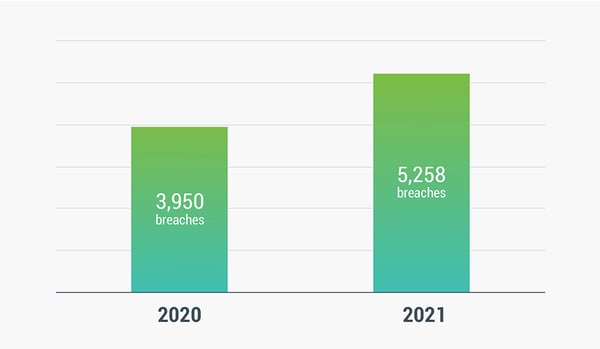
It’s very likely that this is the result of growing ransomware attacks that now include a data exfiltration element changing them from previously being classified as a security incident to now being classified as a data breach. Ransomware now touches all three of the CIA Triad defined as Confidentiality, Integrity, and Availability.
In 2020, ransomware became a very dangerous digital weapon, occurring in 10% of breaches. It has also become a big business, part of a production line of organized cybercrime. With Ransomware-as-a-Service serving as the cyber criminal’s new model, these attacks have accelerated, facilitated by new affiliate partnerships among cyber-criminals.
The DBIR report is one of the most anticipated reports each year, with security professionals, researchers, IT leaders, and CISO’s waiting to see if the security investments they have made will help them become more resilient to cyber-attacks. This year, it is also great to see the continued alignment to the Center for Internet Security (CIS) controls to help provide a better mapping to how you can reduce the risks and become more resilient.
It should also be noted, the report now includes an improved impact section to show how the incidents and data breaches impacted the organization whether it was the loss of business, the cost of the incident, or stock value.
If you are interested in comparing the key takeaways from last year’s report, you can check out my blog: 5 Top Takeaways from the Verizon Data Breach Investigations Report 2020.
Here are my top three key takeaways from the 2021 Verizon DBIR report, along with my recommendations and analysis highlights.
Takeaway 1: Everyone is a potential victim and humans are the top target
Every year, it is clear that everyone is a potential target since no company is too small or too big for cyber criminals to exploit and extort. In a year like no other, the COVID-19 global pandemic has forced many companies to adapt to a remote working environment – increasing their risks from cyberattacks. As employees started working remotely and organizations enabled remote access, the report shows a significant increase in social engineering attacks targeting employees with over 30% of data breaches using social engineering and basic web application attacks not far behind.
Data Breach Summary:
- 85% of breaches involved a human element
- 13% of non-DoS incidents involved ransomware
- 3% of breaches involved vulnerability exploitation
Targeting user credentials is the most favored technique of cyber-criminals. Taking over a user’s credentials allows cyber-criminals to evade detection and bypass security, slipping through cyber defenses under the disguise of an authorized employee. Wanting to be as efficient as possible, cyber criminals continue to use the most common techniques that have the lowest cost enabling them to stay hidden for as long as possible. Attackers no longer hack into your networks – they simply log in using stolen credentials.
Cloud Assets were a top target more than on-premise
Cloud assets are a top target for cyber criminals as more organizations accelerate their migration to cloud services in the wake of COVID-19.
Cybersecurity awareness is a top priority and is working
Organizations must continue to invest in people and cybersecurity awareness training. It is no longer just about meeting simple checkbox training goals. We need to create a cybersecurity culture within the organization where employees are not afraid to ask for help or to report potential security incidents. We must empower our employees to be a solid frontline defense so that when incidents do occur, they report them quickly, helping to stop attacks at the beginning, rather than responding to security incidents once the damage is done and brings the business to a complete stop.
Takeaway 2: Privilege abuse and misuse top cause of financially motivated security incidents
Over-privileged users remain one of the biggest risks to organizations that both internal employees and external attackers continue to abuse. Cyber-criminals want to cause as much damage as possible, stay hidden for as long as possible, and hide their tracks. To achieve this, attackers target privileged accounts. Once compromised, privileged accounts allow them to easily move around the network while hiding in plain sight.
Organizations often default to giving employees more privileges than they need, with most accounts only protected with a simple password created by a human. The challenge we face is that humans too often choose predictable, re-used passwords with simple variations that make it all too easy for attackers to crack them or compromise them with brute-force attacks.
In far too many cases, local administrator accounts are exploited in security incidents and data breaches. Organizations tend to overlook the power that local administrator access gives employees and attackers. A local administrator account is only a few steps away from elevating to a full domain administrator, which provides access to the keys to your kingdom. In many organizations, local administrator accounts are not even monitored, nor do they have additional security controls in place to protect them.
Here are the top common causes of data breaches:
- Poor access management
- Insecure applications and APIs
- Misconfigured cloud storage
- Overprivileged users
- Shared credentials
- Password only security controls
- Securing third-party access and remote employees
- Shadow IT
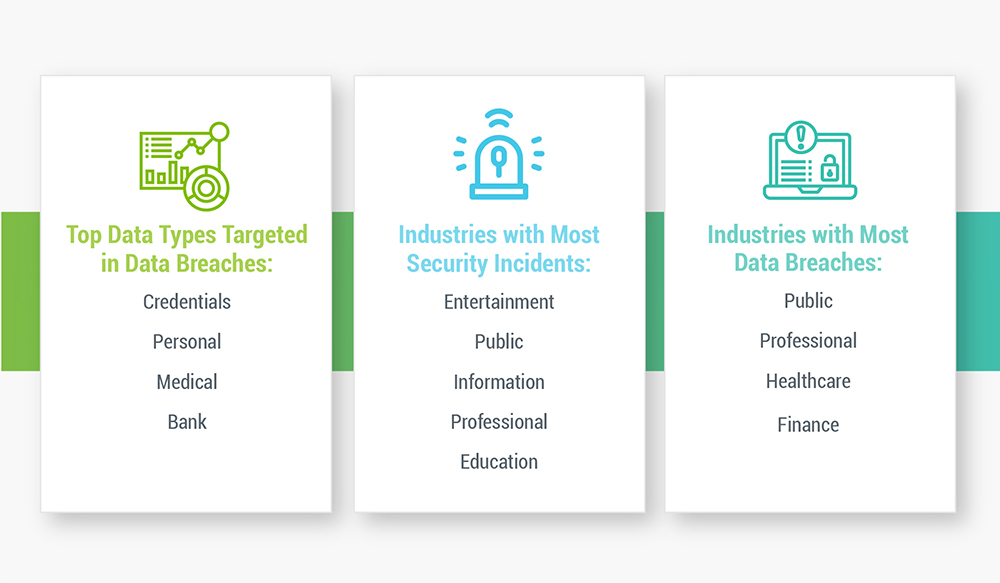
Top data types stolen via privilege misuse:
- Personal
- Medical
- Internal
- Bank
Takeaway 3: Phishing, ransomware, and web app attacks on the rise, driven by pandemic and security challenges
In the past year, we have seen social engineering, ransomware, and web app attacks increase at record levels. These threats put organizations at risk both reputationally and financially. Today’s cyberattacks have evolved from opportunistic attacks resulting from unsuspecting victims clicking on an email pretending to be from legitimate internet service to a targeted digital weapon that attackers use to get control of compromised endpoints and steal sensitive data.
Once a user is compromised, attackers then deploy ransomware—typically using domain admin credentials—to infect as many systems as possible, including digital backups bringing the victim’s business to a complete full stop.
Ransomware is now a big business, part of a production line of organized crime
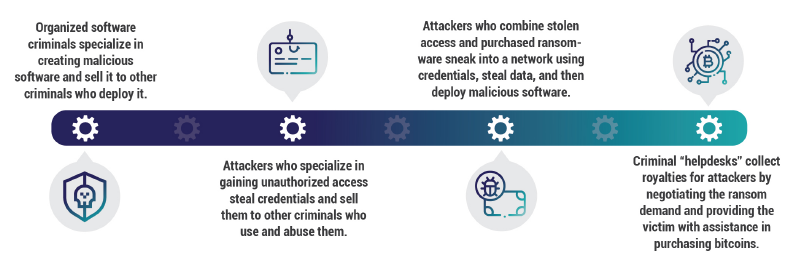
In recent months ransomware creators have also been establishing an affiliate program or partner program which has led to an increase in “ransomware as a service.”
Increase in attack actions:
- Human (85%)
- Credentials (61%)
- Phishing (11%)
- Ransomware (10%)
Financial Impact of data breaches:
- BEC – 95% costing between $250 – $984,855
- CDB – 95% costing between $148 – $1,594,648
- Forensics – 95% costing between $2,402 – $336,499
- Legal – 95% costing between $806 – $53,691
- Ransomware – 95% costing between $69 – $1,155,775
Bottom line: security incidents and data breaches cost organizations money. The DBIR report notes that breaches also impact a company’s stock price, indicating that breached companies underperformed in the stock market by approximately 5 percent.
If you are interested in learning more about ransomware, check out this blog: New Ransomware Model Presumes Honor Among Thieves. It includes my recent session from RSA on a Real-World Ransomware Incident.
When we all work together, the global community wins
It is reassuring to see the DBIR report aligning with top industry standards such as the Center for Internet Security (CIS) Critical Security Controls and the MITRE ATT&CK® framework. It enables mapping them to appropriate controls to be much easier and allows organizations to make the report actionable.
This report reflects the hard work that CISOs and security professionals have been doing to safeguard our data assets during a very difficult time from ever-growing and evolving cyberattacks—especially ransomware. Even in the midst of a global pandemic, cyber criminals around the world have not reduced their attack efforts, so we must continue to be ever vigilant.
This valuable report is another reminder that we must continue to work harder and become more resilient to minimize the risks from cyberattacks. The great work done by the Verizon Team on collecting and analyzing this data continues to help the industry evaluate the past year’s performance and consider what we all must do to make the world a safer place online.
Download the full 2021 Verizon DBIR.

FREE TOOL
Cybersecurity Incident Response Template



