Least Privilege
Table of Contents:
- Defending against 3rd-party data breaches
- Striking the right balance
- Too many over-privileged users increase cyber risk
- What does least privilege access control do?
- Important steps BEFORE implementing least privilege
- Key benefits of least privilege
- Other benefits of least privilege
- Least privilege vs zero trust
- Least privilege vs need to know
- Least privilege and the PAM Lifecycle
What is Least Privilege?
Least Privilege is a cybersecurity term that describes the concept of restricting user and application access to privileged accounts through various controls and tools, without impacting productivity or requiring IT help desk support.
What is the Principle of Least Privilege?
The Principle of Least Privilege (PoLP) is a foundational security principle that ensures users receive only the access needed to fulfill their roles. By following PoLP, organizations limit access to essential data, resources, and applications, granting users merely the minimum permissions required for their tasks, and bolstering overall system security.
Least privilege is intended to prevent “over-privileged access” by users, applications, or services and help reduce the risk of exploitation should user credentials be compromised by an outside attacker or malicious insider. Thus, users are granted only enough authority for an entity to complete a specific task or job. The least privilege model can also help curtail costs and increase efficiency.
Least privilege is your best defense against third-party data breaches
Bad actors and cybercriminals focus on compromising privileged accounts associated with access by third-party vendors. Instead of just targeting one enterprise, cybercriminals are paying more attention to vendors that have multiple clients such as cloud services, and payment platforms.
Examples:
Sunburst - In the highly publicized hack known as Sunburst, nine government agencies and 100 private sector companies were breached in one of the most sophisticated and well-planned operations that involved injecting a malicious implant into the Orion Software Platform with the goal of compromising its customers. Evidence points to compromised user credentials as the entry point for nation-state cybercriminals to exploit this breach.
AMCA - In another dramatic example, American Medical Collection Agency served as a third-party provider of billing services for large healthcare companies such as Quest Diagnostics, LabCorp, and others.
A data breach at AMCA that started in August 2018 and carried through until March 30, 2019, resulted in compromising the private information of 20 million Americans, including name, date of birth, provider, and balance information.
The breach resulted in AMCA losing its largest clients, numerous class action lawsuits, and huge penalties for noncompliance with HIPAA regulations. AMCA eventually filed for bankruptcy while its clients suffered damage to their reputations as well as their bottom line.
Unfortunately, many organizations do not have a defined process or program to help manage the risks associated with giving third-party access.
Putting in place a least privilege management program aided by purpose-built least privilege software enables your organization to restrict access by third-party vendors to only what is relevant for completing their assigned tasks. The key, of course, is to manage the least privilege access control process so that productivity can be maintained while monitoring access for any unusual or suspicious activity.
See which IT systems and users have higher privileges than they need
You must strike a balance when implementing a least privilege security strategy
IT Security tries to balance the needs of the business while at the same time securing and protecting your organization’s most valuable assets. To secure the organization, IT Security usually attempts to limit access to overprivileged users and privileged accounts. However, this can create conflict between IT Security and the rest of the employees as they attempt to complete their tasks with reduced access.
Privileged accounts exist everywhere in your IT environment. In many cases, users may not even realize the type of access they possess. They only know that when access is denied, they can’t get their work done. Hackers and cybercriminals target these privileged accounts because once compromised, they provide the ability to move across your systems and networks undetected. And all it takes is one compromised user with local administrative privileges to gain full control or steal your most sensitive information.
One of the keys to finding a balance between productivity and security lies in your choice of least privilege management software—when it’s easy to use you’re more likely to deploy all the features and craft a productivity/security balance that’s perfect for your organization.
Too many over-privileged users increase the business’s cyber risks
Organizations today typically face major challenges when implementing a least privilege policy because built-in limits on access can impact employee productivity. One thing is clear: when an employee has too many privileges you typically do not hear from them, but when privileges are limited or restricted and the employee is unable to access an account, launch an application or connect to a printer, the IT help desk will surely be the first to know.
Unhappy employees are quick to call the help desk when they are unable to perform their jobs. This usually results in the IT help desk making the user over-privileged, and while they can now perform their job it is at the increased risk of turning a simple incident into a major catastrophe. Should the over-privileged employee fall victim to a cyber attack, the attack could easily escalate to the entire organization.
What does least privilege access control do?
Least privilege access control provides the key to limiting risk within an organization. It helps build upon a Zero Trust security model and includes a risk-based security strategy. Zero Trust is a place where most organizations should begin, and this means that all access requested by any user or system to the network, services, applications, data or systems is verified, and trust is built but continuously challenged if the trust is changed.
This requires organizations to classify users and systems into trust risks, for example, different security controls between employees, contractors, suppliers, or departments.
Cybersecurity classifications of trust and accepted risk can be dynamic. That is, you create different policies or rules across the enterprise for identities, services, applications, data, and systems.
The more access you have or request the more security controls you must satisfy before you get access. You have the choice of trust as always, verify, or always audit, depending on how much risk you must reduce.
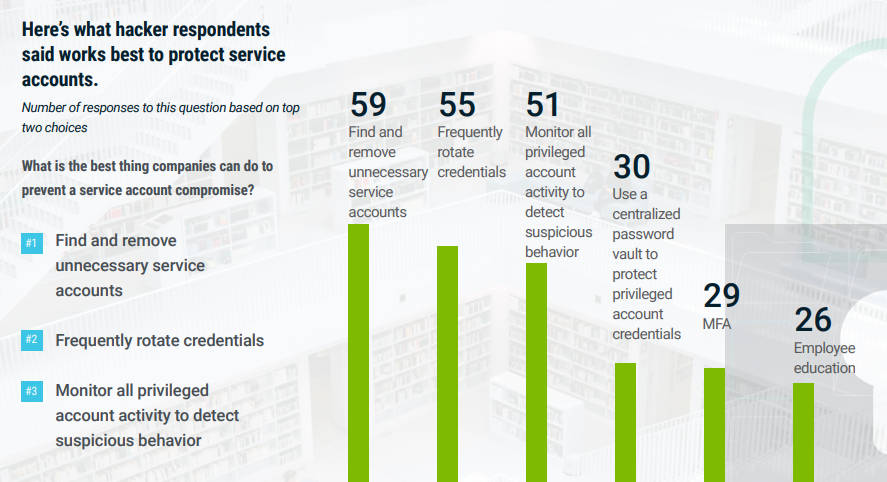
What steps must be taken before implementing least privilege?
There are several important steps to take before implementing a least privilege strategy:
1. Discover all Admin and Local Admin Privileges
2. Inventory all your devices and software
3. Monitor privileges and learn their usage
4. Replace privileges with automation policies
1. Discover all Admin and Local Admin Privileges
First, you should automatically discover all admin and local admin privileges across the environment, and this includes privileges inherited via group memberships. It is important to know what employees, devices, software, services, applications, and hardware have privileged accounts provisioned. This will help identify where your organization is compliant with industry compliance requirements, and possible gaps that need to be secured further.
2. Inventory all your devices and software
It is critical that you know what software is deployed and how software gets deployed, so knowing where it was installed from in the first place is a good way to get to know the organization’s risks. Was software installed from SharePoint, a USB device, downloaded from the internet, via an email or deployed using a software delivery solution?
This will help determine what applications you have, whether you are properly licensed, trusted vendors your organization depends on, suspicious applications, and the most common method chosen by users to install the software. Depending on your organization’s IT Policy, you might want to determine at this stage your preferred method of deployment, and what should be restricted.
3. Monitor privileges and learn their usage
Before enforcing restrictions or least privilege you will want to learn about the common usage: which employees are actively using their privileges and which users are potentially over-privileged. Now you can determine which users’ administrative privileges need to be replaced with policies to ensure that they can continue doing their job without any disruption.
4. Replace privileges with automation policies
Once you have audited the environment you can start to remove or reduce privileges from users who no longer require them. For those who actively require them, you can replace privileges with policies that allow the task to be elevated on demand without the user becoming over-privileged.
By combining both Privileged Access Management (PAM) and Application Control you can control access to devices, services, applications, data and hardware, and control which actions they can perform.
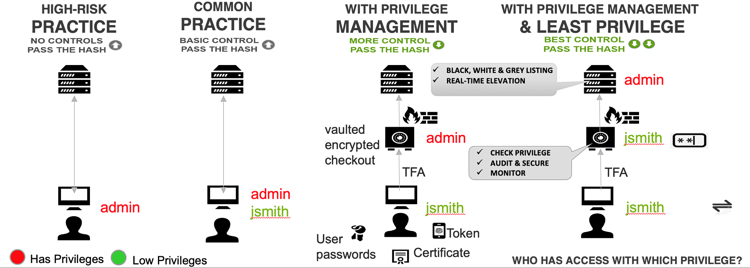
What are the key benefits of the least privilege approach to security?
The concept of least privilege delivers several key benefits to organizations that adopt this approach to their cybersecurity. Enforcing least privilege with application control, for example, helps organizations reduce security threats and maintain productive employees who can continue performing privileged tasks and actions under trusted predefined policies.
When you implement least privilege with application control, your employees are empowered and continue to be productive with increased security working in the background to prevent cyber threats. The key benefits of implementing a least privilege strategy with application control include:
- Reduced costs—save time and money by managing users securely.
- Empowered, happier employees who can perform their tasks without encountering roadblocks.
- Fast-tracked, demonstrable compliance through automated reporting to satisfy auditors.
- Improved security that blocks cybercriminals and malicious insiders from exploiting credential compromise.
Other benefits of the least privilege model:
Least privilege harnesses technology to reduce risks caused by cyber fatigue
Globally, organizations are being challenged by an ever-growing cyber threat landscape and are experiencing serious cyber fatigue. Their employees are dealing with constant information overload about cyber attacks, ransomware, identity theft, and phishing scams. They reuse previous passwords (under pressure to constantly change passwords every time there’s news of a data breach), which increases both cyber risks and cyber fatigue.
Cyber fatigue is occurring at all levels of the organization, from the CISO looking for metrics on the company’s exposure to cyberattacks to the IT Security team trying to force employees to be more secure. The organization must meet compliance, and employees need to perform their daily tasks, but nobody knows if the next email is the one that contains malware or might attempt to steal their identity or their credentials.
Least privilege access control enforces safer practices and reduces the likelihood of your organization experiencing cyber fatigue-induced errors.
Least privilege reduces the burden of responsibility on employees
For years, employees across all departments in most organizations have routinely practiced risky behavior, usually unintentionally and unknowingly. They do this by clicking on attachments or links within emails not knowing what might happen next; by logging into internet services using the same password they use for their Facebook account, corporate email, and bank account; or by simply plugging in a USB stick they got for free at the last conference they attended.
Despite efforts to raise cybersecurity awareness and train users on secure behavior, 25% of your employees will open phishing emails, and more than one in ten will click on an attachment that contains malware. These types of successful social engineering attacks are just one reason why employee workstations and personal devices are the most vulnerable part of your IT systems.
By implementing privileged access control, you relieve employees of some of the responsibility for your organization’s security and simultaneously reduce your risk level.
Applying the principles of least privilege also provides these benefits:
Compliance management: Most organizations today need to satisfy various compliance requirements and regulations. A structured least privilege strategy will help organizations meet most compliance and regulations requirements for restricting administrator access, so look at your least privilege strategy as a fast track to meeting most of your compliance security requirements.
Time-consuming patch management: Patch management is one of the most repetitive, challenging tasks that all organizations must carry out, yet they continuously fail at staying current. As most exploits on Windows require local administrative rights, least privilege security helps reduce the risk of more than 90% of Microsoft Windows Vulnerabilities. So, you can focus on only those vulnerabilities that are exploitable without local admin rights. This saves an organization both time and money as it becomes more effective at patching critical vulnerabilities.
Malware and Ransomware: Risks will be reduced because the user will not be able to execute untrusted applications, so an accidental click on that malicious email attachment will be prevented from infecting the system or any other system on the same network.
Third-party vendors: Exposure to third-party vendor risk will be properly managed with a least privilege control model that helps reduce the risk of breaches from non-compliant vendor practices.
In summary, a strong least privilege strategy will:
- Reduce costs: Save time and money by managing users securely.
- Produce empowered, happier employees: They can perform their duties without encountering roadblocks.
- Fast track compliance: Automate reporting will satisfy auditors.
- Improve security: Block cybercriminals and malicious insiders from exploiting password compromise.
What's the difference between least privilege and zero trust?
Least privilege enables enforcement of a zero-trust risk-based security model whereby once a user is verified, the user’s access is limited to only what’s necessary to accomplish the specific task or job. If any user action requires more access than granted via policy rules, permissions to elevate privileges are strictly controlled and monitored.
While simple in concept, enforcing least privilege in IT environments can be highly complex and involve hundreds, if not thousands, of users, applications, and services that need access to privileged permissions.
Zero trust assumes any user or system that accesses the network, services, applications, data, or systems starts with zero trust. To gain authorized access, trust must be earned by the prospective user through verification. For example, verification can require two-factor authentication. In this instance, a user provides a password but then must take an additional step by using an authentication application.
When new devices are introduced on the network—and before they obtain access to any resources—they must first identify and verify themselves based on various security controls. The more sensitive the resources to be accessed, the more security controls they must satisfy.
Cybersecurity should always begin with zero trust, ensuring that only authorized access is permitted. After verification of identity is established, users can be classified according to the access they need to perform their jobs. Least privilege can then be enforced through policies granting specific access.
What's the difference between least privilege and need to know?
The term “need to know” refers to a business justification or reason for a group of individuals to access systems for a specific purpose. This is tied to a recognizable business outcome and can be vetted by the system owner, the requestor's management, project leadership, or another source of authority.
While” need to know” indicates the user has a legitimate reason to access something, least privilege is the enforcement method that limits access to that something, and what the user can do with that something.
For example, if a user is recognized as having a legitimate business need to access ('need to know') customer data, a least privilege policy will determine what KIND of access that user should get to customer data. Should it be read-only? Give the ability to update or delete customer data?
The goal of least privilege enforcement is to give the user the least amount of privilege necessary to get their job done. In most organizations, privileges are role-based and assigned in bundles such as: administrator, super-user, user, auditor, or other designation.
How does Least Privilege with Privileged Access Management work in a PAM Lifecycle approach?
Adapting the PAM Lifecyle to the least privilege model will greatly increase your odds of least privilege implementation success. This diagram illustrates the key steps involved in achieving least privilege security success in your organization.
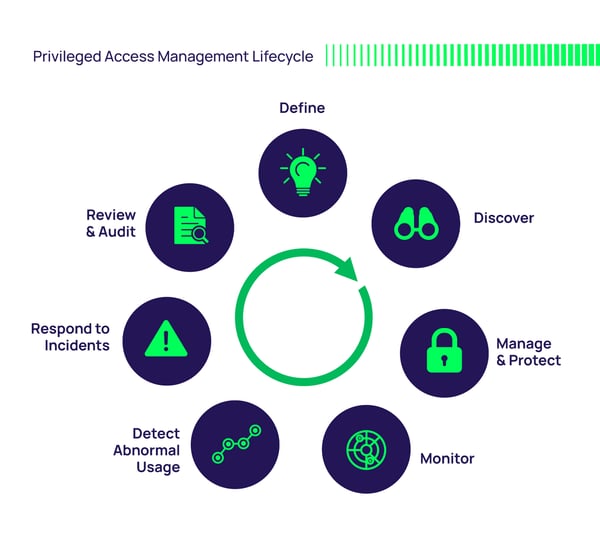
The steps in the PAM Lifecycle are detailed here:
The Privileged Access Management Lifecycle and Path to Maturity
- Define privileged access and accounts
- Discover privileged accounts continuously
- Manage, protect, and control
- Monitor usage
- Investigate abnormal behavior
- Respond to incidents
- Review and evaluate privilege access controls
Many organizations start their journey to achieving least privilege with a discovery project. They determine which endpoints and local users have admin rights, what applications are in use, and whether they require admin rights to keep a record for future maintenance efforts.
Once through the discovery phase, organizations can then:
- Create an allowlist: add all the applications and processes that you trust.
- Implement a denylist: block known bad files. Or incorporate a reputation service.
- Create a restrictlist: Manage unknown areas with your restricted and automated workflow to allow approved apps to run and to block malicious apps.
- Set contextual policies that align with your risk assessment.
- Users may change roles or departments—accommodate these changes in your least privilege plan.
- Don’t limit yourself to domain-controlled endpoints only.
- Remember child processes.
- Integrate workflow into your existing tools.
- Measure success, coverage, and existing risks.
- Enable user interactive elevation requests/workflows.
More Least Privilege Resources:
Blog Posts
Least Privilege Examples
Free eBooks
Least Privilege for Dummies
Solutions
Zero Trust and Least Privilege
Tools
Least Privilege Discovery Tool
Whitepapers
Achieving Least Privilege with CIEM and Enterprise-Scale PAM
Global State of Least Privilege Cybersecurity
Products:
Privilege Manager - Endpoint privilege management and application control software
Implementing Least Privilege shouldn't be hard
