Identity and Access Management (IAM)
What is Identity and Access Management?
Identity Access and Management (IAM) is a broad term for ensuring the right people or machines are properly identified and given access to specific resources for a given length of time according to enterprise policies. In most cases, IAM refers to managing human users' identities—typically customers and employees who are accessing products and services online. By comparison, Privileged Access Management (PAM) focuses on human and non-human accounts that need access to privileged or more sensitive information, primarily by IT administrative staff.
For example, some of your users, like your IT administrators, will receive privileged identities—identities that are given higher levels of access on the network. Others, such as your sales team and employees, will receive standard user identities that do not allow them to customize network settings, access server, or use any network privilege. Thus, Privileged Access Management is an integral part of any IAM program.
PAM and IAM implement logical security controls to protect access to accounts and endpoints. PAM and IAM are very similar, distinguished mainly by a different set of users and endpoints. IAM focuses on all employees and their workstations. PAM focuses on administrators and the servers and network devices they manage. There is overlap of course, since an administrator is also an employee.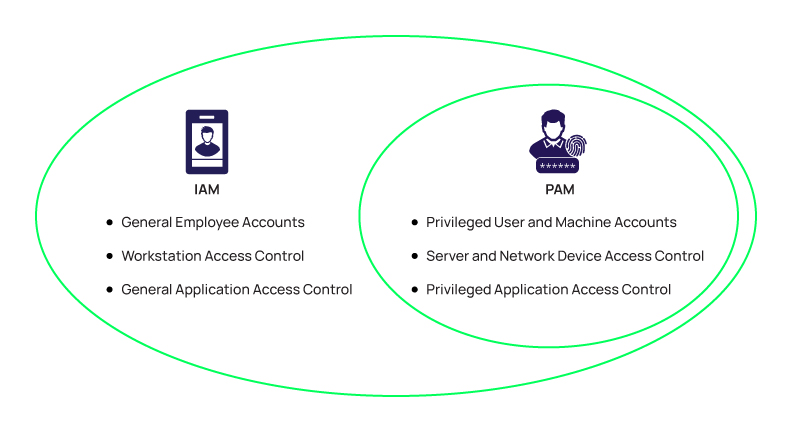 In this context, one could argue that PAM is a subset of IAM, focusing on a subset of users and endpoints.
In this context, one could argue that PAM is a subset of IAM, focusing on a subset of users and endpoints.
Identity and Access Management systems give IT administrators tools and technologies to manage a user's role, track the user's activities, generate reports on those activities, and enforce policies continuously. IAM system software is focused on administering proper and secure user access across the entire enterprise and to ensure compliance with corporate policies and government regulations.
Identity and access management has been evolving rapidly over the past few years. Until recently, traditional IAM approaches revolved around a username/digital signifiers such as an email address, device, date of birth, and a password. In our increasingly cloud-oriented digital environment, this traditional approach has become less effective. There are several reasons why the username/password combo no longer provides secure access. Cloud and mobile computing, for example, have dissolved the traditional boundaries of the cybersecurity perimeter.
How does PAM integrate into IAM best practices?
With nearly 80% of security incidents and breaches involving compromised user credentials, organizations now recognize that a robust PAM solution must be an integral part of any IAM strategy and work together with IAM tools to assure access to information is governed by a least privilege strategy. This helps to 1) ensure only the right people who can prove their identities via IAM, and 2) they are given the appropriate level of access to the right systems governed by PAM solutions that enforce least privilege.
As more companies rely on remote workforces and cloud applications to power their businesses, there is also an increasing need to extend the benefits of PAM to different end-users and groups. Additionally, the very nature of what's considered "privilege" has evolved and is no longer considered just for IT users.
Therefore, PAM and IAM best practices have evolved to a point where security professionals prioritize secure vaulting of credentials for privileged accounts and secure access to privileged data and applications.
Conventional PAM models focused on IT users, accounts, and systems that reside at the heart of the enterprise, along with IT-centric privileged accounts—like domain admin accounts. However, as compromising user credentials has become a primary target for cybercriminals and malicious insiders, the IAM and PAM distinction has started to blur. That's because all users (including employees, executives, contractors, and third-party vendors) these days can be considered privileged users. Even one user account protected by a password can be exploited by an attacker to elevate privileges and access an organization's most critical and sensitive data.
IAM, PAM, PEDM... What do all those acronyms mean?
How has PAM expanded the scope of identity and access management programs?
PAM ensures users have the precise access privileges required for their job. The requirement for precision has evolved as security awareness improves. As notable large-scale breaches leveraged compromised accounts or as internal users misused their privileges, the requirement for precision grows.
The impact of the COVID-19 pandemic and the related growth in the number of employees working remotely has also increased the role and importance of PAM as part of an IAM program. This has helped organizations extend PAM security by expanding privileged access controls for employees who require administrative access and remote privileged access for third parties, including vendors, contractors, service providers, and business partners.
PAM software enables organizations to precisely apply the principle of least privilege to mitigate the risk from breaches and insider threats, ensuring that the right person has the right access to the right resource at the right time for the right reasons. PAM best practices use PAM software to control access to privileged accounts, rotate credentials after each use, and monitor, record, audit, and analyze privileged access sessions and activity.
For example, suppose a new major data breach occurs. In that case, that puts many organizations' identities and credentials at risk. Combining IAM and PAM can increase the security controls required and rotate existing passwords of suspected high-risk credentials. Organizations must reduce the risk of brand damage, leaks of PII, theft of proprietary information, or prevent unintentional access to sensitive data. This requires a comprehensive program that links ALL types of identities seamlessly across the enterprise, associating the identity and auditing the precise access they have.
Ideally, the right governance fosters productivity by eliminating barriers and seamlessly moves users and systems through checkpoints while managing security risks. IT and Security ops teams will benefit significantly from automated programs. Unified, comprehensive, and automated programs will reduce burdens and human error and accelerate time to remediation.

FREE EBOOK
Privileged Access Management For Dummies
